Movement
beats perimeter.
This domain governs how identities move through systems, how privileges stack, and how trust boundaries are enforced. When it fails, every credential becomes a master key.
Identity, Access, & Trust is where abstract risk turns into real movement.
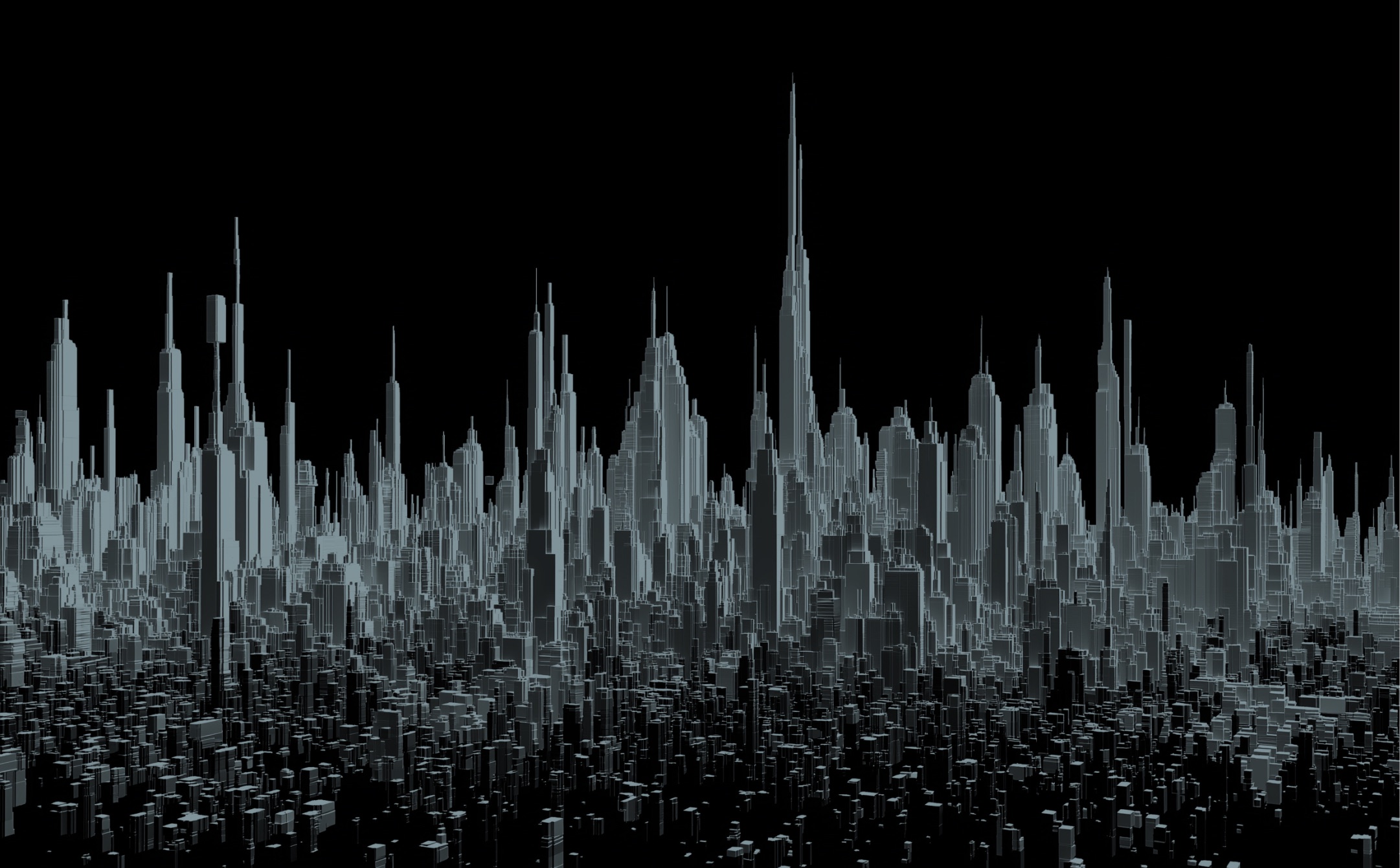
This is the city layer of the operating environment.
Identities traverse systems the way people traverse cities. Access paths form roads, bridges, and choke points. Privileges stack vertically. Trust relationships connect environments in ways that are rarely mapped or intentionally designed.
Perimeters exist, but they are not what attackers exploit.
They move through pathways.
In dense environments, small access decisions compound quickly.
What feels temporary becomes permanent.
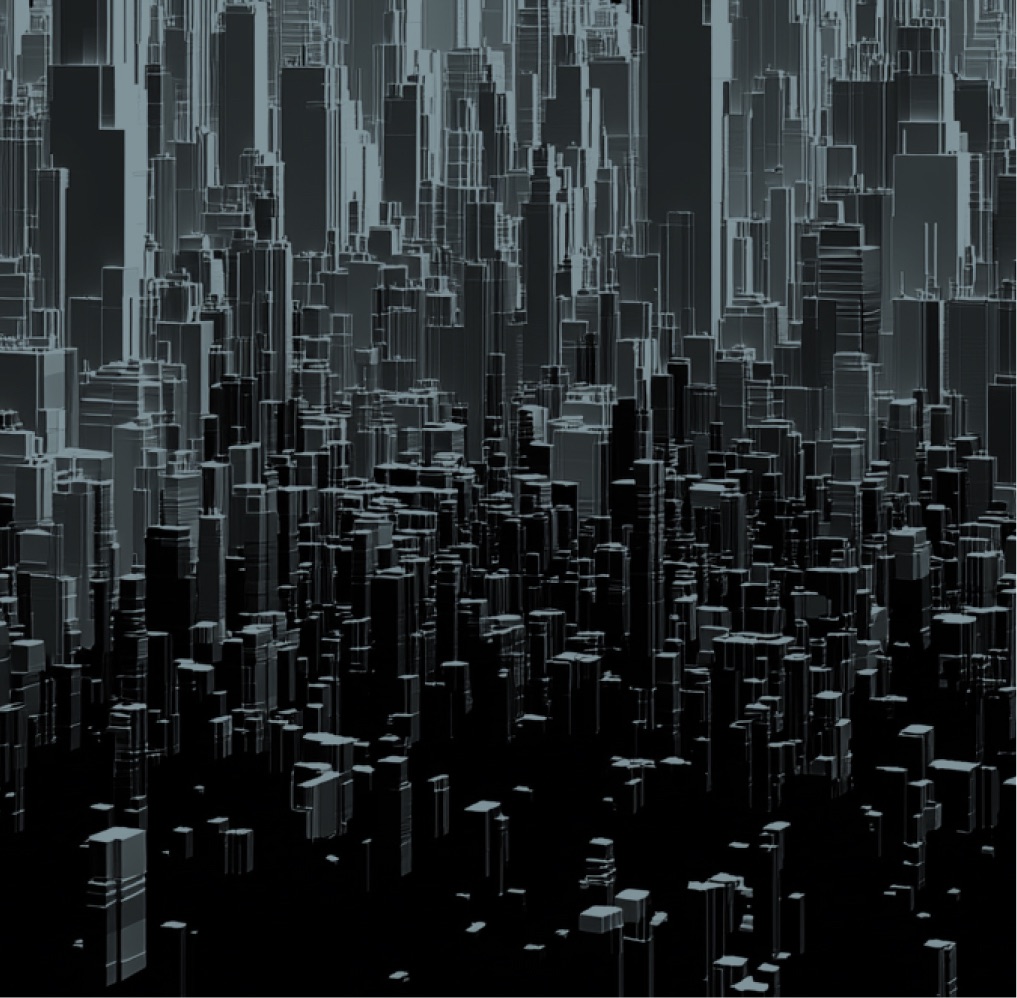
This domain governs how movement is permitted, constrained, and observed.
Identity lifecycle across users, services, and systems
Privilege allocation and escalation paths
Access pathways between environments
Trust boundaries and implicit relationships
Lateral movement potential during compromise
IAT is not about authentication alone.
It defines how far compromise can travel.
Organizations often believe identity problems are solved once authentication is implemented.
They are not.
This domain exists because movement matters more than walls. Once access is granted, every trust relationship becomes a potential route. Over time, privileges accumulate, identities persist beyond their purpose, and pathways emerge that no one intended.
Without intentional control, cities sprawl.
And sprawl is what attackers exploit.
Lateral Movement and Privilege Sprawl
When IAT fails, access expands silently.
Privileges are granted to “unblock work.”
Service accounts persist indefinitely.
Trust relationships multiply without review.
How Failure Manifests
Excessive standing privileges
Orphaned and forgotten identities
Unmapped trust relationships
Privilege escalation during incidents
Rapid lateral movement after initial access
Why Downstream Domains Cannot Compensate
No amount of hardening or vulnerability management can compensate for unrestricted movement.
When identities can traverse environments freely, attackers bypass controls by design. Every downstream domain is forced to respond after movement has already occurred.
This layer determines whether compromise stays local or becomes systemic.
Path Control and Segmentation
CDA treats identity as a system of movement, not a static directory.
We focus on:
Explicitly mapping access paths.
Constraining privilege by function and time.
Segmenting trust boundaries intentionally.
Reducing standing access wherever possible.
This is not identity sprawl management.
This is movement control.
How IAT Feeds the Next Layer
When movement is constrained, preventive controls can shape outcomes.
When it is not, posture becomes reactive and brittle.
IAT determines whether Security Posture & Hygiene can prevent attacks or only detect them.
This domain is engaged through Missions that establish identity clarity, reduce privilege sprawl, and enforce segmentation aligned to real operational needs.
It is never treated as an IAM implementation project.
It is treated as an access geometry problem.
Identity, Access, & Trust is one layer of a stacked operating environment.
It defines
pathways.
It constrains
blast radius.
It determines how far compromise can move.
In dense systems, structure is survival.

